BurgerSwap被攻击分析
事件影响
-
本次攻击主要是因为burgerswap的智能合约分层时的验证不足,导致被重入攻击成功
-
BURGER-BNB流动池中的BNB和BURGER都被大量拿走,导致流动性不足
-
因为黑客手里有大量BURGER,后续就算官方补充流动性也会因为黑客抛售BURGER而导致BURGER的价格变低
事件信息
此项目由成都链安进行审计
地址对应的tag与解释:
| TAG | 解释 |
|---|---|
| Pancake-BUSDT-BNB-LP | Pancake的BUSDT-BNB流动池 |
| BS-A-Contract | BuegerSwap攻击者使用的合约地址 |
| BS-Attacker | BuegerSwap攻击者的地址 |
| BS-A-Fake-Token | BuegerSwap攻击者的“假币” |
| BURGER | BURGER Token |
| Demax-BURGER-BNB-LP | Demax的BURGER-BNB流动池 |
| BLP-Fake-BURGER | Burger的假币-BURGER流动池 |
| Demax-Fake-BURGER-LP | Demax的假币-BURGER流动池 |
攻击交易
https://bscscan.com/tx/0xac8a739c1f668b13d065d56a03c37a686e0aa1c9339e79fcbc5a2d0a6311e333
事件分析
本次攻击共分成六个步骤:
- 攻击者在Pancake的BUSDT-BNB流动池使用闪电贷贷出6,047个BNB
- 攻击者用兑换出的6,028个BNB在burgerswap的BURGER-BNB池兑换出92,677(直到目前为止没有任何问题)
- 攻击者使用兑换出的近一半(45,452)的BURGER和自己的token创建一个交易对
- 攻击者使用100个自己的token兑换BNB,兑换路径为FakeToken->BURGER->BNB
- 在兑换之前,会调用
_getAmountsOut先计算出来路径上的金额是多少 - 在兑换时会调用"FakeToken"的
transfer方法,此时发起重入攻击,使用剩余的45,316个BURGER兑换4,478个BNB - 在攻击完成之后继续兑换路径上的其他
transfer方法,原本因为4.2步已经使用45,316个BURGER兑换了4,478个BNB,无法再使用45,452个BURGER兑换出4,478个BNB(因为此时的BNB的价格已经升高,应该兑换的BNB更少才对);但是因为此处依然使用4.1步骤计算好的兑换金额,并且最底层的兑换逻辑并没有根据x*y=k的公式进行校验,因此导致又以相同的价格兑换了BNB,即兑换出的BNB变多了 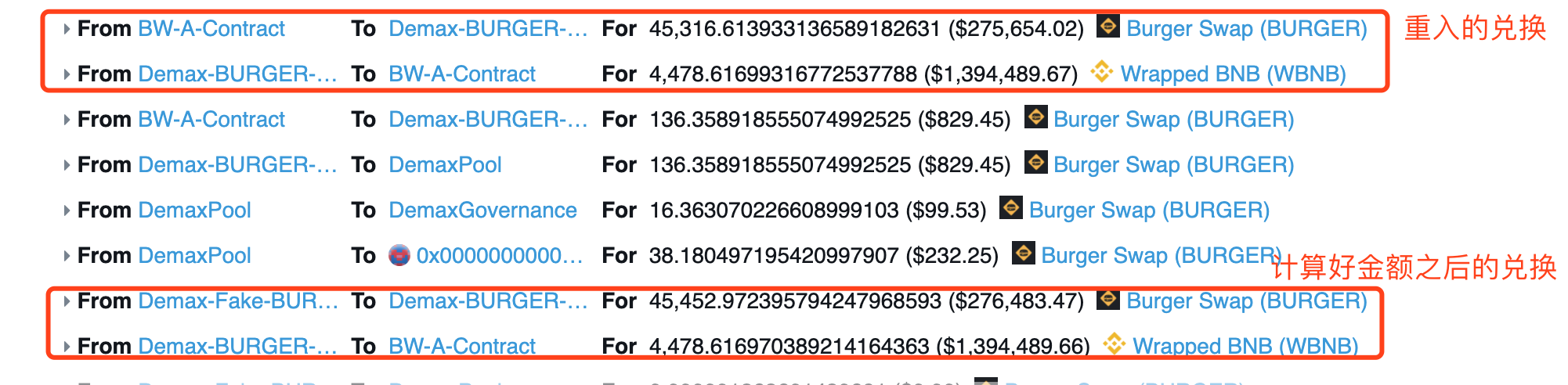
- 在兑换之前,会调用
- 在完成第四步的攻击之后,BURGER-BNB池中的BNB数量变少,BURGER的价格变低,因此攻击者又使用491个的BNB兑换出了108,791个BURGER。(注意第一步使用6,028个BNB才换了92,677个BURGER!)
- 归还闪电贷6,062个BNB(闪电贷归还的金额必须大于借出的BNB)
事件涉及的源码
步骤4的调用DemaxPlatform合约的swapExactTokensForTokens方法如下:
从合约代码中可以看出,在这里已经计算好了所有兑换路径的所有的兑换出的金额是多少,然后调用_swap方法。
1 |
|
步骤4中调用的DemaxPlatform合约的_swap方法如下:
下面的代码展示了在计算好金额之后,如果满足兑换之前的校验就按照计算好的金额在指定的路径进行兑换;最终兑换的逻辑会调用IDemaxPair的swap方法
1 |
|
合约DemaxPair的swap方法如下:
此合约直接根据传入的金额进行代币的_safeTransfer,最终只是校验了一下amount0In > 0 || amount1In > 0。
1 |
|
作为对比uniswapV2的UniswapV2Pair的swap方法如下:
在最后验证了新的x’和y‘的乘积必须大于等于原来的x和y的乘积:x‘ * y‘ >= x * y
1 |
|
作为对比pancakeswap的PancakePair的swap方法代码如下:
在最后不仅有校验进入的金额大于出去的金额,也有乘积的校验。
1 |
|
合约DemaxPair的_safeTransfer方法如下:
此方法会调用token的transfer方法,而本次的攻击就是攻击者自己的token的transfer方法又调用了DemaxPlatform合约的swapExactTokensForTokens方法。
1 |
|
官方后续处理
- 创建新的**$cBURGER**并空头给满足条件的原$BURGER的持有者
- 使用burgerswap的收入以及原本要奖励给团队的burger建造一个价值700万美元的奖励池

